Microsoft is going to release an update which will turn off unsigned LDAP requests on Domain Controllers. This update will be released in March this year (2020). More information here: ADV190023
Although I assume everyone is already using LDAPS instead of LDAP like everyone already mitigated the ADC’s back in December 2019 😉 Here is a guide how to enable LDAPS on the ADC’s.
Some points to remeber:
- The Domain Controllers should have a certificate bound to them so LDAPS is enabled;
- Offcourse you have Load Balanced the Domain Controllers on the ADC’s in the LAN and you point the DMZ NetScalers to this Load Balancer and the LAN ADC’s as well;
- Changing the Load Balancer from LDAP 389 to LDAPS 636 will involve adding certificate to the Load Balancer as well, Carl has a nice article how to load balancer LDAPS Here
- LDAPS is using port 636 and LDAP is using port 389, so a change in firewalls is required.
All reaquirements in place?
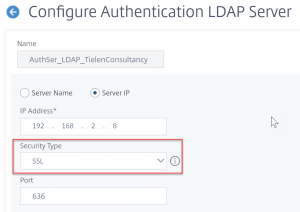
Open your existing LDAP server and change Security Type to SSL. This will also change the port to 636.
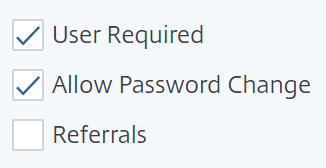
Now it is also possible to allow user password changes. So when the password needs to be changed (I think you can find reasons why) the ADC will ask the users for his new credentials. This check the box:
Update: Yes, you can use TLS over port 389. So no firewall ports need te be changed. But this is not LDAPS but StartTLS. 😉 More information about that topic can be found Here.
How do I confirm #1: The Domain Controllers should have a certificate bound to them so LDAPS is enabled
Open the computer certificate store on the domain controllers and verify if there is a certificate in the personal store.