This blogpost will explain how-to setup Prism Central (2023.4) to use SAML against Microsoft Entra ID (Azure AD) so we can use Sigle Sign On.
First we start with the authentication methods most of the time useD in Prism Central:
- Local Accounts;
- The Admin account or own created normal accounts. Please try to avoid this;
- Active Directory;
- AD User Groups have a role assign in the cluster so they can do admin tasks;
- This is a preferred method as all tasks can be pinpointed back to the actual user who did it 😉
Now lets connect Prism Central against Microsoft Entra to have SSO capabilities.
Before you continue make sure you have setup the FQDN in Prism Central. More information here: https://portal.nutanix.com/page/documents/details?targetId=Prism-Central-Guide-vpc_2023_4:mul-pc-management-c.html
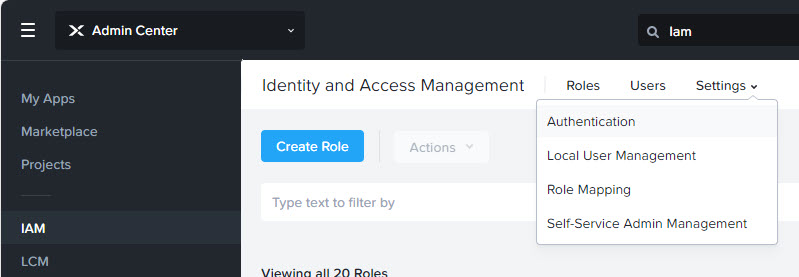
In Prism Central go to IAM in Admin Center and select: Authentication under Settings.
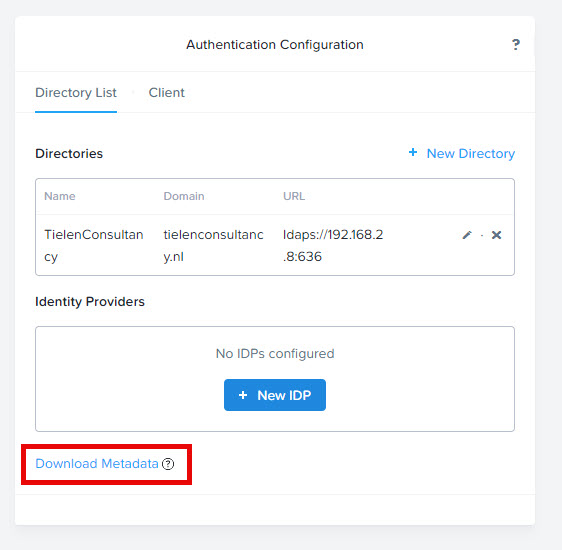
Click on “Download Metadata”
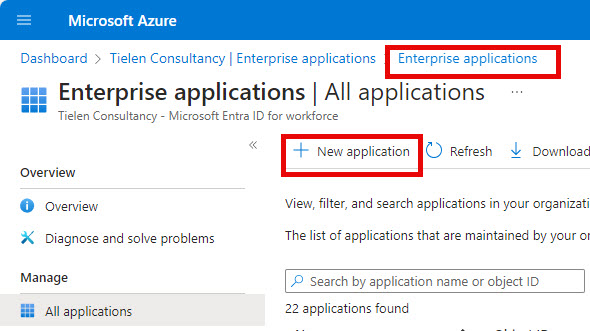
Now head over to Microsoft Entra ID and open pane “Enterprise Applications”. Click on: New Application.
Click “Create Own Application” and full out as described in the screenshot below:

When the custom application is created open “Assign Users and Groups”
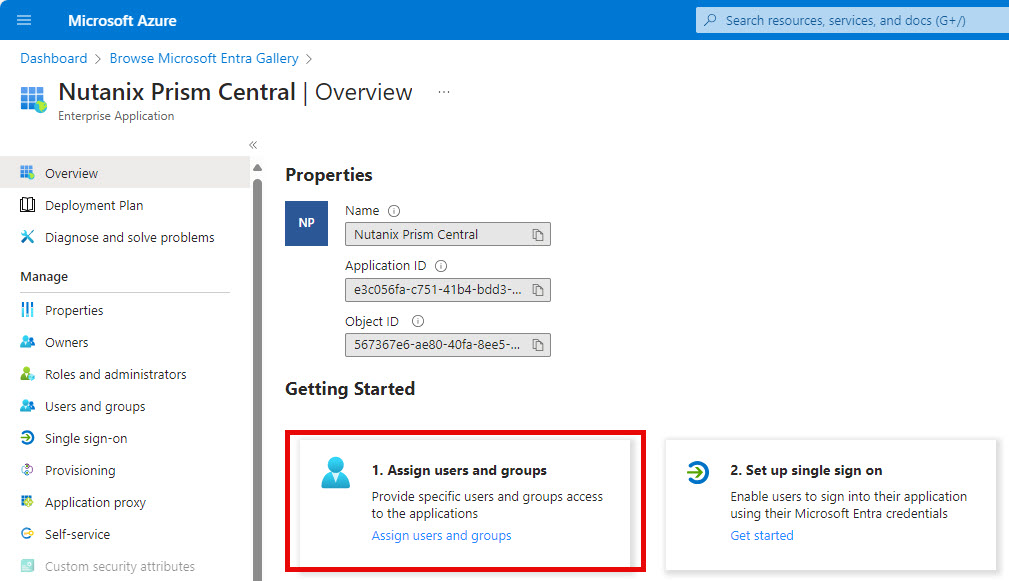
Add the groups you want to add (the users in this group can login into Prism Central). When done click on : Single sign-on and then on SAML.
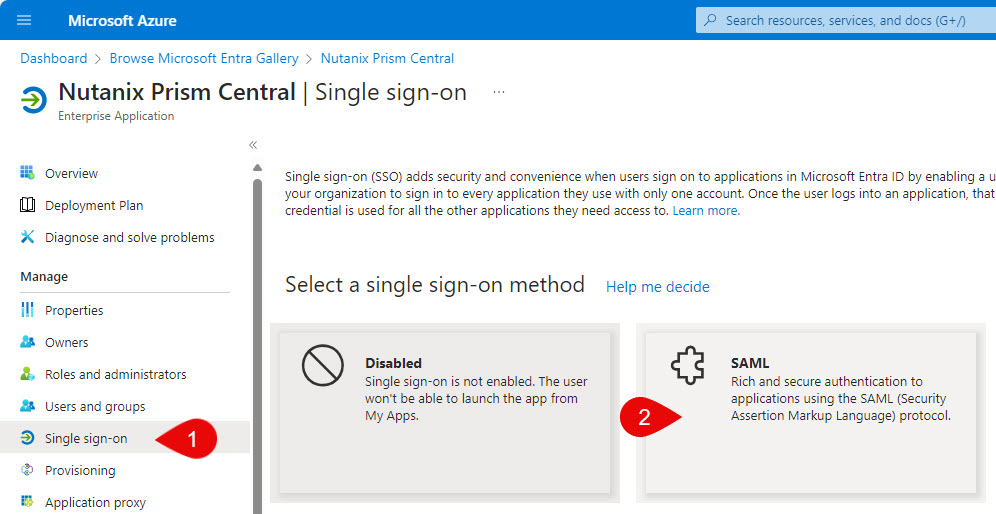
Upload the downloaded metadata file.
When the metadata is uploaded click on save.
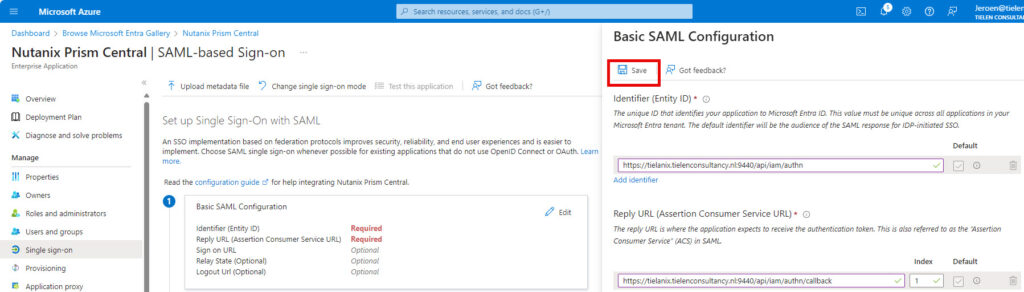
Scroll down to number 3 and download the Federation Metadata XML
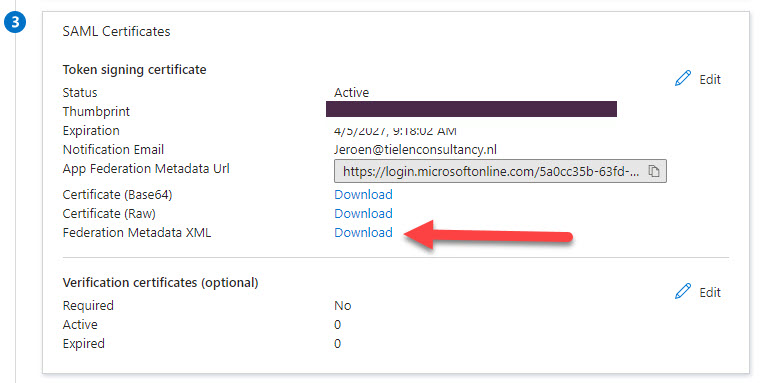
Go back to Prism Central IAM –> Settings –> Authentication and click on “+ New IDP”
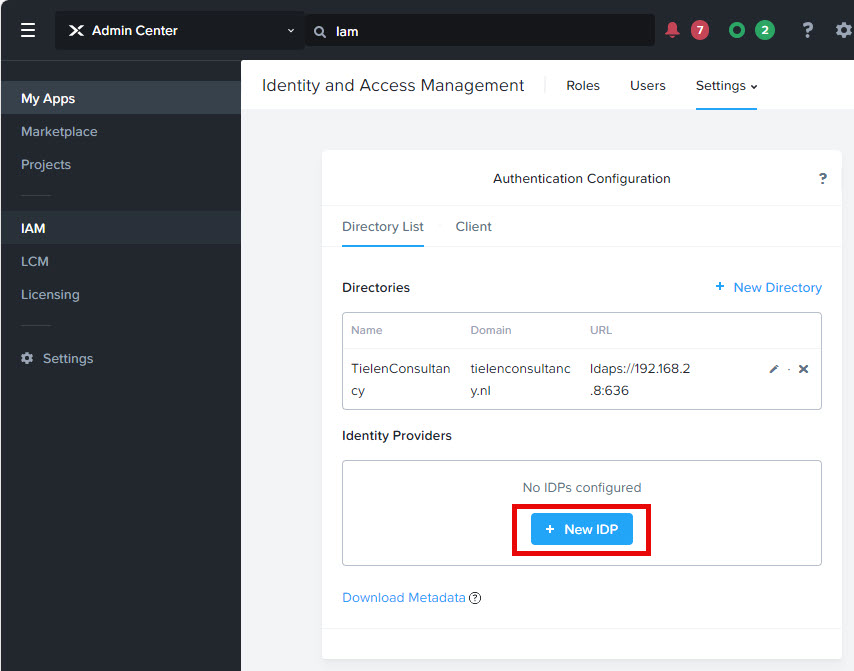
Give the configuration a name and click on “+ Import Metadata”. Upload the metadata file downloaded from the Enterprise App create above. Don’t forget to click save.
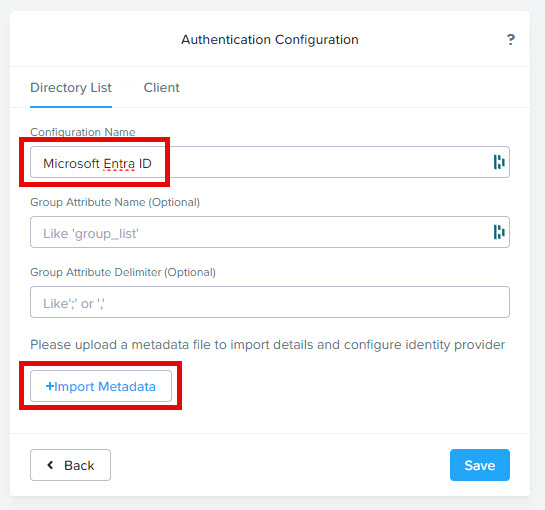
It should look like this:
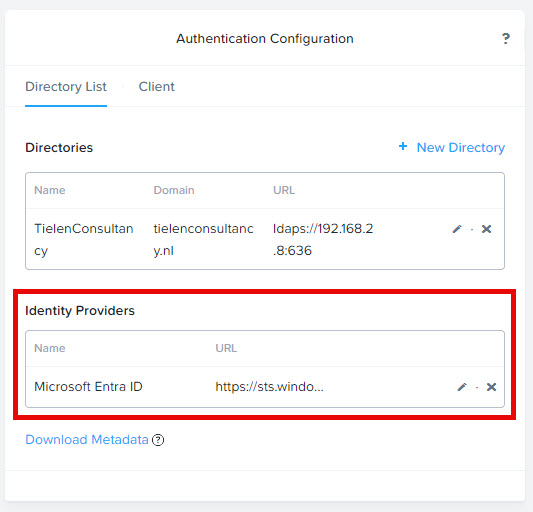
Next step is to create the role mapping.
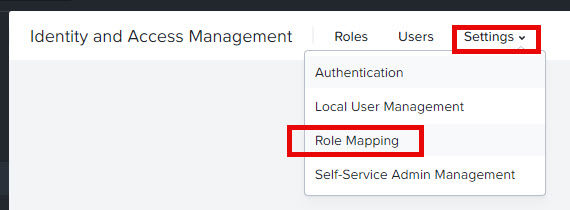
Click add role mapping and fill in as below (use your own UPN of course):
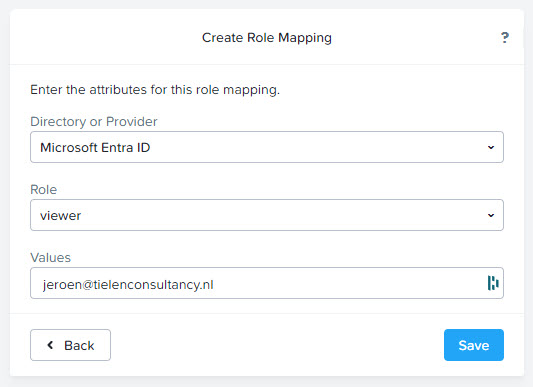
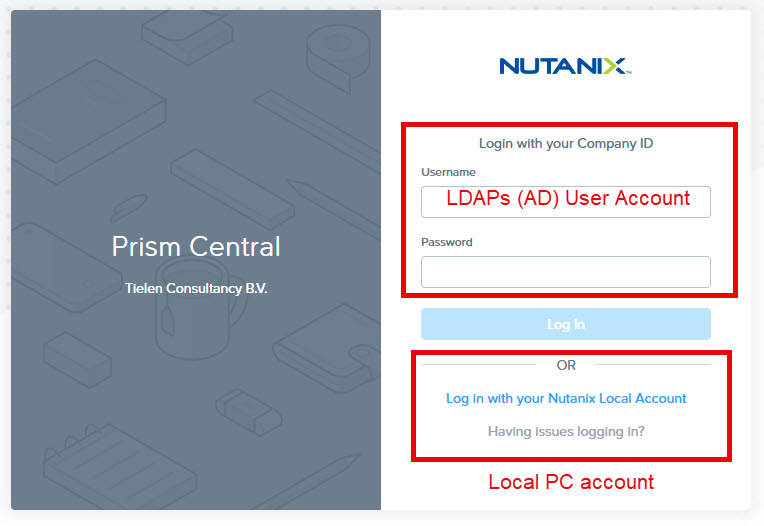
After clicking save you can logout of Prism Central. The login screen will look like this:
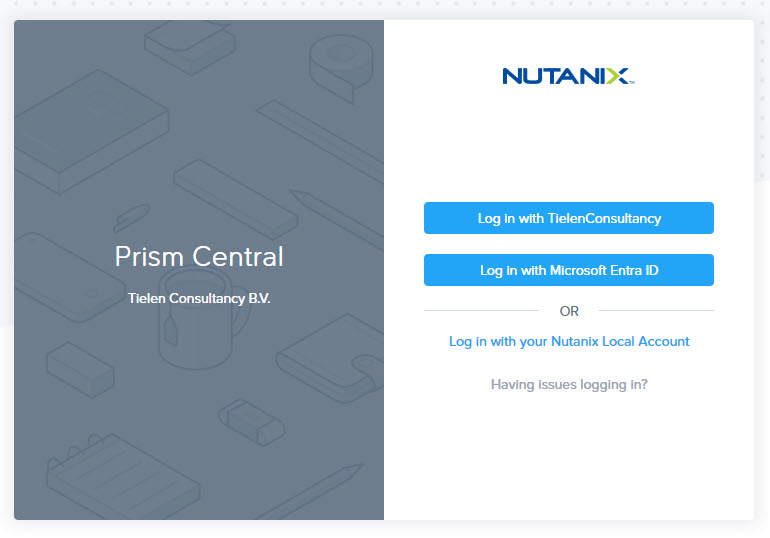
As my management workstation is azure AD joined I will automatically login with my user account into Prism Central when I click the “Log in with Microsoft Entra ID” button. Here video how the SSO will work. (Keep in mind, my workstation is Entra ID joined, so I’m already authenticated against Entra ID)
Unfortunately we cannot add a user group for the role mapping. So each and every admin must be added in the rol mapping screen. (Or go all out and create custom claims in Entra ID and create role mappings based on the claims names. But this will not log the username in the audits from Prism Central)
For now all is working but if you want you can finetune the configuration a bit more. In the SAML assertion there are multiple claims. Prism Central is only looking for the name identifier. So we can remove all, unused, claims in the enterprise app.
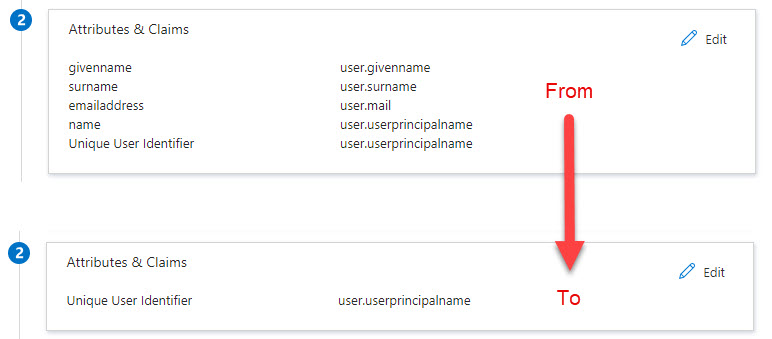
When you configure conditional access on the enterprise app you can filter even more when users are allowed to logon.



Great instructions…been looking for this for a while.
I kinda got everything working, but when I am in the IdP onfig and click on the “download Metadata” button it generates my prismcentral.companyname.com as it’s IP address X.X.X.X.
Now I tried to change the metadata file from IP address to prismcentral.companyname.com and then upload it to Entra, but it still tried to find my IP vs the name.
I noticed when I go to: https://prismcentral.companyname.com:9440/PrismGateway/services/
it references my IP address again instead of domain name in the RESTful services.
Any idea on this?
You need to set the fqdn for prism central, and make sure this is on the dns. https://portal.nutanix.com/page/documents/details?targetId=Prism-Central-Guide-vpc_2023_4:mul-pc-management-c.html
Great instructions.
When I download Idp Configuration from PC, for some reason it generates my xml file as an IP address instead of the dns name I use to access prism.
So then when I upload that to entra, entra gets confused and expects an IP.
I tried to change it in the xml file to my dns name and in entra, but no luck.
I also noticed that in https://pc.companyname.com:9440/PrismGateway/services/ it lists my IP in the RESTful services.
Wondering how i can use my dns name like you do in your instructions?
Thank you…after following your link I was able to set the FQDN to my dns name In PC Management. I then download the xml file from Prism again and it shows the DNS name in the .xml file and not the IP so that was good.
I made sure I re-imported in Entra, but I still get the following error: Application with identifier ‘https://:9440/api/iam/authn’ was not found in the directory ”.
I rebooted PC even.
I wonder if support would help me otherwise…
Yes if you are running the commercial version then you are good to go with support. Or if you are at .next this week in Barcelona let me know and I will help you.