The Citrix XenMobile (Citrix Endpoint Management) on-premises appliance comes default with no hardening. This means that running SSLLabs against the mdm ssl_bridge you will get the following score:
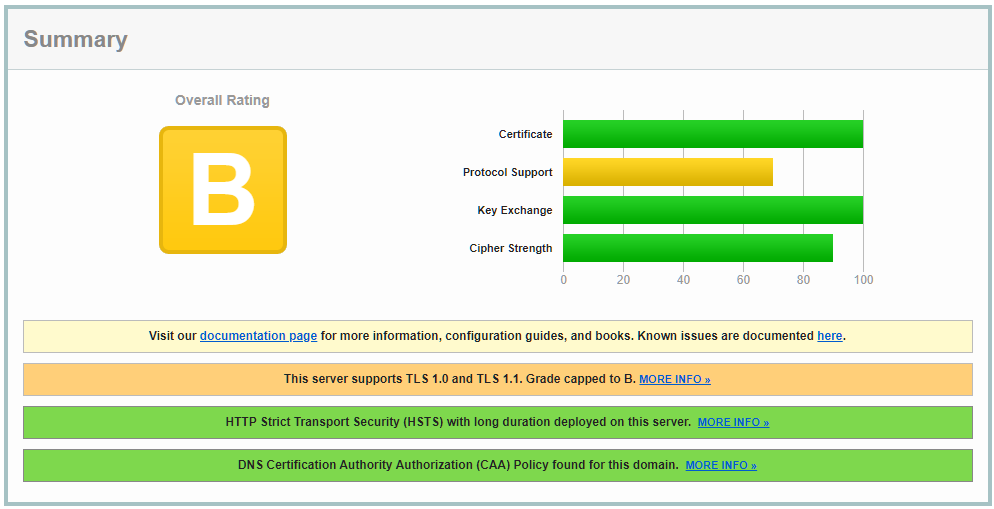
As you can see not the best setup 😉 I noticed that a lot of XenMobile, on-premises, environments aren’t hardend. So here is the simple guide to fix this.
Launch an ssh session (or console via the hypervisor) to the first XenMobile appliance and log in.
Go to: 2. System -> 12. Advanced Settings -> 2. Custom Ciphers.
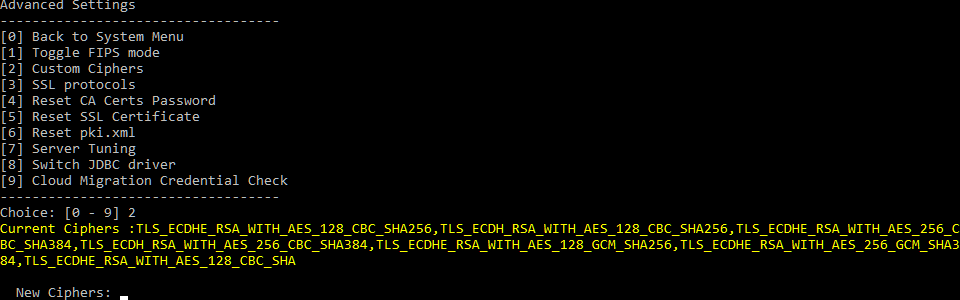
Here you see, in yellow, the default ciphers which are enabled. We need to change them to: TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256,TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
![]()
Dont restart the system yet. Go to menu option: 3. SSL protocols.
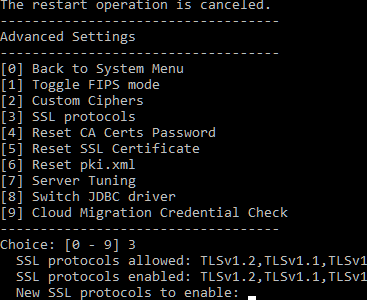
Here you will see that default TLS1, 1.1 and 1.2 are enabled. We need to change this to: TLSv1.2
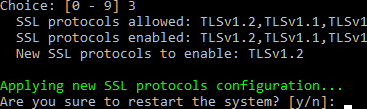
Restart the box and do the same on the second node of the hazelcast cluster.
Run SSLLabs and the results would be:
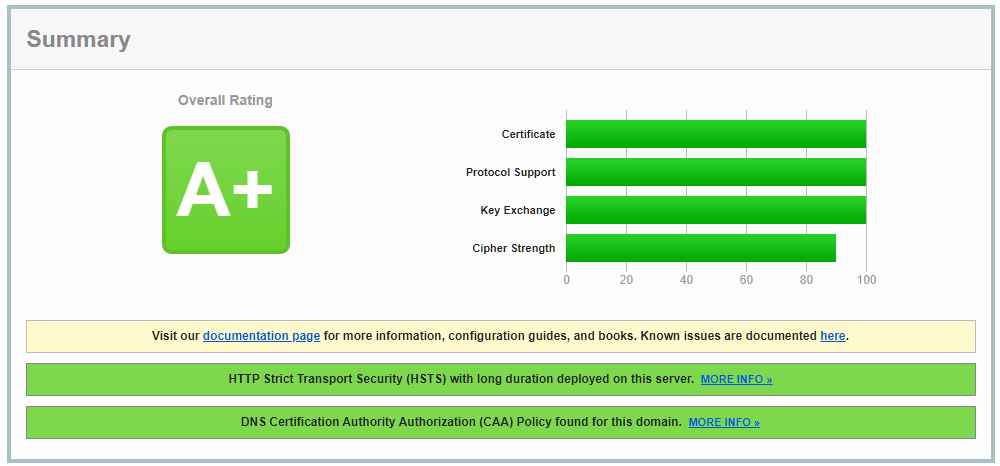
Don’t forget to harden the gateway seperate.
Here are the original ciphers and protocols so you can copy/paste when needed te revert:
Original Ciphers: TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256,TLS_ECDH_RSA_WITH_AES_128_CBC_SHA256,TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384,TLS_ECDH_RSA_WITH_AES_256_CBC_SHA384,TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256,TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384,TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA
Original Protocols: TLSv1.2,TLSv1.1,TLSv1
On reducing the cipher suites on the XM servers to only the two TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256,TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384, found that iOS devices are unable to connect to the store within Citrix secure hub. As soon as all the ciphers are returned on the XM servers to the original default Cipher settings, secure hub can then successfully connect back to the Store within secure hub. By removing and adding the available Ciphers on the XM server from the default list found that it would only work when one of the following where added to the list.
TLS_RSA_WITH_AES_256_CBC_SHA,TLS_RSA_WITH_AES_128_CBC_SHA256,TLS_RSA_WITH_AES_256_CBC_SHA256
However as soon as one of these ciphers added the maximum security score achievable is a B. Any idea why you did not experience a similar issue as the SSL Bridge connection for the mdm is going straight to the XM servers, did you test connecting to the Citrix secure hub store after making the modification to the ciphers.
Hi,
I did not experienced that issue. Are you up to date with iOS versions and Secure Hub?
Jeroen.