Ubiquiti has a little article on the site how to add yout own ssl certificate to your Unifi controller. But they made it a bit to complex 😉 Read article.
First let me explain what kind of certificate the Unifi controller wants to have:
- The controller works with a keystore file. In this file the whole certificate chain and key file must be included;
- The keystore file must have password: aircontrolenterprise (can be changed);
- The keystore file must have alias: unifi.
The keystore file is located in: /usr/lib/unifi/data (Linux) or %UserProfile%/Ubiquiti Unifi (Windows).
Open the current keystore file in “Keystore Explorer“. If you can’t open it with password: aircontrolenterprise then you need to make sure the controller is using this password. Follow these steps to do this:
- Rename current keystore file so the controller can’t use it anymore (or just delete it);
- Edit /usr/lib/unifi/data/system.properties and add line: app.keystore.pass=aircontrolenterprise
Note: You could also choose your own password here; - Restart the controller and there will be a new keystore file generated;
- try to open this file in keystore explorer with the correct password.
If you can open the file with the given password we need to replace the current self-signed certificate with your own certificate.
First create 1 cer file which holds the certificate and intermediate certificate(s). Open a new text file in notepad, or your favorite text editor. Paste the certificate followed by the intermediate certificate(s). The file should look like this:
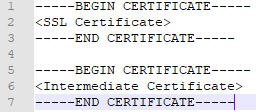
If you have more than 1 intermedate certificate just add them all. Start with your own SSL certificate and follow the chain up to the Root CA.
Note: You don’t have to provide the Root CA certificate as this should already be present on the endpoints connecting to your Unifi controller.
Now we need to create a PFX (PKCS12) file which holds the just created cer file and the key file. If you don’t have already please install openssl.
The command to create the PKCS12 file is: openssl pkcs12 -export -in <you_cer_file_with_the_chain>.cer -inkey <you_key_file>.key -out <name_it>.pfx
Choose you own password for this. This could be different than the password used in the Unifi controller.
Now switch back to keystore explore and delete the unifi entry.
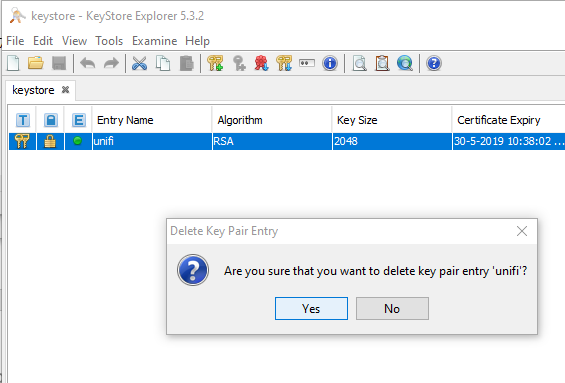
Click: Tools –> Import Key Pair –> PKCS12. Locate the PFX file and give the password you gave during creation of the pfx file.
The Key Pair Alias should be: unifi
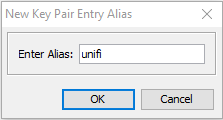
And provide the new password. This should be the password you have set in the Unifi controller (aircontrolenterprise).
Save the keystore file and copy it to the Unifi controller. Restart controller and you are good to go 🙂
Where do I get the .key file?? it like you missed a step.
The .key file is part of your own certificate. It holds the private key of your certificate. This article does not descibe the process of creating a certificate signing request etc etc.
Thanks for the Quick Reply. Your article got me 75% there. Where i got stuck was using openssl to generate the PFX file. After quite a few failed attempts and after banging my head on the wall for about 2 hrs, I ended up replacing your openssl steps with installing a cert on the server and then used windows to export and create the PFX. I then used Keystore explorer to import the PFX windows made into the keystore following the steps you outlined.
Haha yeah Ubiquiti should make this easier. But you got it working now?
Yep, since this work out to be an all GUI way of doing it, I should do a write up for the windows Controller installs that are out there.
This write up is also for the Windows versions. Only file locations are different. But these locations are in this og post ;).
I tried my wild card certificate but it doesn’t work what’s wrong?
Could be miljons of things. What specific error do you get or what isn’t working?
Unifi controller says the certificate is invalid
Do you have a link to a screenshot?
Yes I have. (Link removed by Jeroen)
Hi alessandro,
It is nog the controller who give that error but your browser. It looks like your domain name doesn’t match your certificate name. Or you dont have the SAN field filled in the certificate. Google Chrome is monitoring on this, and if this is not present it will present an error. More info on this subject: https://support.google.com/chrome/a/answer/7391219?hl=en
The certificate is a wildcard *.mydomain.it
Do I have to create an ad hoc certificate for Unifi controller?
Wildcard certificate are working fine (I’m using a wildcard as well) but your certificate must be correct. Can you provide the url to me? Then I will have a check. If you dont want to type it here you can email the url to jeroen@tielenconsultancy.nl. I dont need credentials, only the url is enough and I have a look what is wrong. 😉
Hi Allessandro,
You url is not a valid url for SSL connections. You need to provide the FQDN and not only the hostname. more info: https://serverfault.com/questions/269838/what-is-the-difference-between-a-hostname-and-a-fully-qualified-domain-name
Hi,
Custom SSL works, but Cloudkey every few days replaces my SSL with self-signed one. Why? How to stop it? I have to upload keystore with custom ssl every few days, and then restart unifi service.
Hi Slawek, I dont have a cloudkey so I dont know. I’m running the Unifi controller on a linux virtual machine.
I feel so close to figuring this issue out but keep hitting a snag. I created the certificates to be signed and got them signed by SSLs/Namechap, I can access the keystore, I got all my certs together in one file, but not exactly sure how to make or get my key file…. Should I extract it from the certificate I got back from SSLs? Only showing public key for that one.
Got them all installed via Java but then get protocol error, so I’m trying this method hoping it will work.
Thanks in advance!
Hi,
I wanted to inquire if you can tell me by following your steps from OP by deleting the keystore then it will recreate a new one. If the new one is recreated, will it have a new self signed time stamp?
I have tried to post in ubnt forum: https://community.ubnt.com/t5/UniFi-Routing-Switching/SSL-Certificate-default-renewal-for-Unifi-Controller-UCK-gen1/m-p/2683881/highlight/true#M134172 but no one seems to be answering nor ubnt support to answer my question. They just said not supported.
I understand that you don’t have UCK cloud key but wanted to see when the key is gone, will it generate a new fresh one and can be used right away. Not worrying about prompt as long the self signed certificate gets renewed.
Thanks in advance!
Correct. It will created a new one. You can test it yourself by backing up your current keystore file and remove it from the controller.
Thanks. I will try it tonight when I get home. I should have asked here to begin with 🙂
Jeroen,
It worked :). Simple removal, restart and it will generate a new self signed key for another 10 years.
I will play around later with a custom one.
Cheers.
Now you have 10 years to create a custom one 😂😂
Jeroen, thank you so much for this article, it really cleared things for me.
Cheers
Vojtech
Your welcome. Have fun with the controller
Hello Jeroen,
Maybe a trivial question, but please write if it’s possible.
All devices on the network should have SSl certificates installed to browse the internet safely.
Is it possible to install the certificate on a Unifi controller not to install on computers?
I have UniFi Security Gateway pro-4 and two 24 port switches.
Regards
Christopher
No. Internet is, by default, not safe. Certificates installed on the network will only say that those devices are who they say they are. Requested websites must have certificates installed (TLS certs).
Best regards, Jeroen.
Thanks, this helped a lot.
You’re welcome. 👍🏻👍🏻
Our CCTV server died and has been rebuilt but has a different name. I’ve been told by our web host that we need to re-key the certificate. I’ve downloaded and installed keystore explorer but there are no keyfiles in the location mentioned for Windows servers.
To re-key the current cert I need to generate a CSR – is there a way to do this in Ubiquiti?
Thanks in advance
Hi Mark,
Yes to re-key (create a new key-pair) to need to create a new csr. You can do this via multiple methods. I dont know is the ssl tools are present in a ubiquiti controller at the moment. Cant test it either as I switched over to Cloud Ket Gen2+.
Best regards Jeroen.
Hi Jeroen
Did you get it to work on your Cloud Key Gen2 + ?
I have install the SSL certificate and rebooted the key and USG Pro but I still only see the std. certificate called CloudKey. How do I change the std. certificate to the new one ?
Best Regards
Martin
Hi Martin,
I dont have the Cloud Key Gen2+ anymore. I switched over to an Unifi Dream Machine Pro. But this could be because you have the wrong type of key-pair. This should be a RSA key. Try to convert the key to RSA and try again.
Best regards, Jeroen.
Thanks for the tips Jeroen! I took this one step further and created a script to do this all on the command line. That way I can update the certs automatically. I already have Let’s Encrypt doing all the renewals elsewhere.
https://github.com/gcarey3/copy_certs_to_udmpro
Instructions were very straight-forward, but when I replace the original keystore with the modified one (containing my key/cert/int) on startup, that keystore file is overwritten with the self-signed certificate. Any thoughts?
The blog is a bit old and not up to date for the new unifi controllers.
Wanted to say I just tried this process on controller ver 7.3.76 running on Ubuntu and the directions worked perfectly the first time.