At the moment we all know how to score an A+ in ssllabs.com for our NetScaler Gateway but can we also score an A+ on securityheaders.io?
My test environment currently has this score on ssllabs.com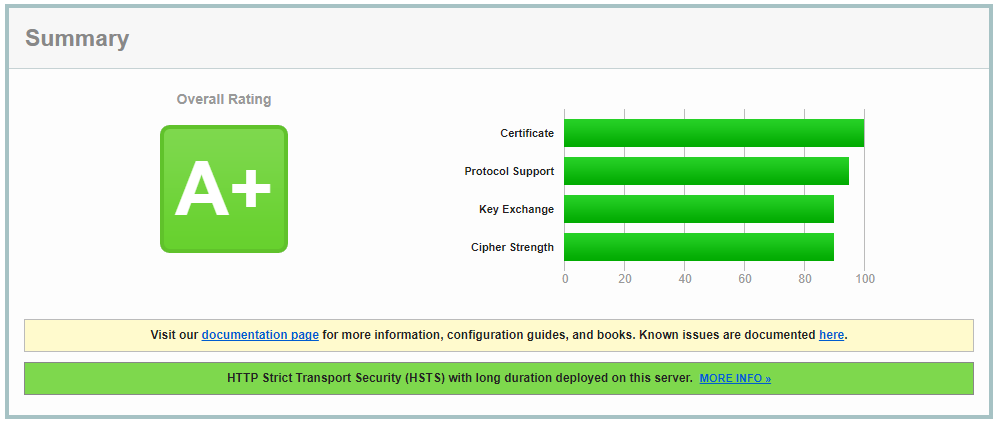
And this score on securityheaders.io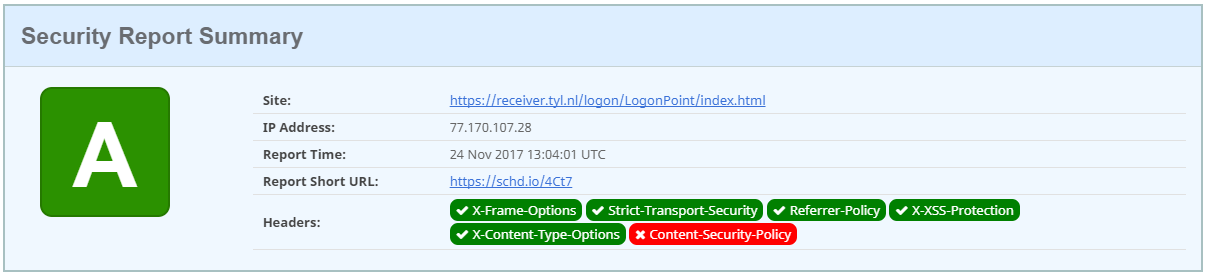
As you can see I already did some preparations before this post. 😉
To configure the headers on your vServer add them as rewrite policies:
add rewrite action RA_Insert_STS_Header insert_http_header Strict-Transport-Security "\"max-age=157680000\""
add rewrite action RA_Insert_XSS_Header insert_http_header X-Xss-Protection "\"1;mode=block\""
add rewrite action RA_Insert_XContent_Header insert_http_header X-Content-Type-Options "\"nosniff\""
add rewrite action RA_Insert_Referrer_Header insert_http_header Referrer-Policy "\"SAME-ORIGIN\""
add rewrite action RA_Insert_X_Frame_Header insert_http_header X-Frame-Options "\"SAMEORIGIN\""
add rewrite action RA_Insert_Expect_CT_Header insert_http_header Expect-CT "\"enforce,max-age=30\""
add rewrite policy RP_Enforce_STS TRUE RA_Insert_STS_Header
add rewrite policy RP_Enforce_Referrer TRUE RA_Insert_Referrer_Header
add rewrite policy RP_Enforce_XSS_Header TRUE RA_Insert_XSS_Header
add rewrite policy RP_Enforce_XContent_Header TRUE RA_Insert_XContent_Header
add rewrite policy RP_Enforce_X_Frame TRUE RA_Insert_X_Frame_Header
add rewrite policy RP_Enforce_Expect_CT TRUE RA_Insert_Expect_CT_Header
No rocket science in here 😉 But how to get that Content-Security-Policy green.
First we need to understand what the CSP is doing. There is a nice website explaining this: https://content-security-policy.com/
Done reading? So you now know what it is and what it is doing? Great.
To keep this blog post short. You aren’t getting an A+ score on your NetScaler Gateway vip if you enable CSP the correct way. But the best setting for me at the moment is the following:
add rewrite action RA_Insert_Content-Security-Policy insert_http_header Content-Security-Policy "\"default-src 'self' ; script-src 'self' 'unsafe-inline' 'unsafe-eval' ; style-src 'self' 'unsafe-inline' 'unsafe-eval';\""
add rewrite policy RP_Enforce_Content-Security-Policy TRUE RA_Insert_Content-Security-Policy
If you bind this to you NetScaler Gateway vServer the results would look like this: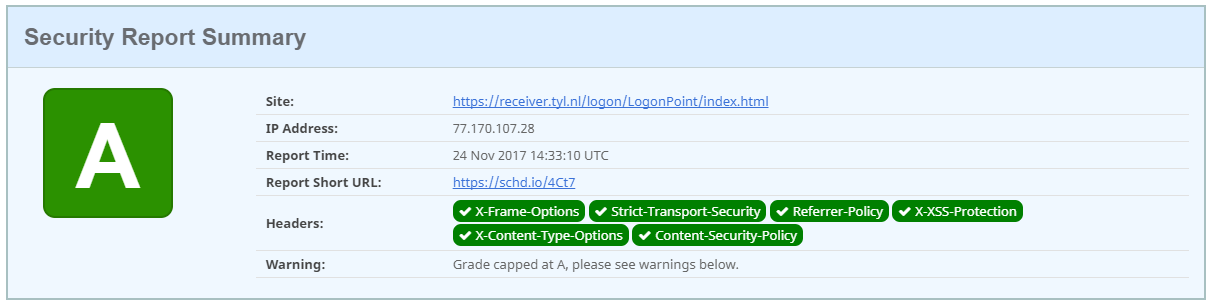
It’s not an A+ but only an A. But this is a correct Content-Security-Policy. And I think you should not read further but implement this.
You do get this warning, but we can “safely” ignore this as Citrix is a security company 😉 Or isn’t????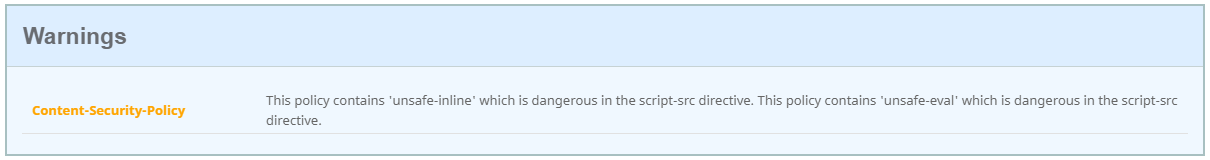
Scoring the A+ for a content switch or a loadbalancer hosting some websites isn’t that hard. You just have to figure out the correct CSP. But for the NetScaler Gateway seems impossible.
If we bind this simple, but correct, CSP the whole CSS markup of the NetScaler Gateway page is gone.
add rewrite action RA_Insert_Content-Security-Policy insert_http_header Content-Security-Policy "\"default-src 'self';\""
If I bind an empty CSP to my NetScaler Gateway I do get my A+ score and the site is still working. Offcourse this is not a working CSP header but my OCD can sleep now 😉
add rewrite action RA_Insert_Content-Security-Policy insert_http_header Content-Security-Policy "\"\""
As long as Citrix implements “unsafe-inline” and “unsafe-eval” scripts in the Gateway we could not get it to work properly.
Update 27-11-2017: I’ve added the new Expect-CT header. For more information about this new header: https://scotthelme.co.uk/a-new-security-header-expect-ct/
Hi Jeroen,
Thanks for this great article. I applied the policies to our netscaler gateway and we now have an A+ too. I have one question though.
When I check our Authentication Virtual Servers, we use them for OWA, at securityheaders.io it looks like the headers are not detected. Although I did bind the rewrite policies to the LB VS. Any ideas on how I can check whether my policies are working?
Thanks.
-Sebastiaan
Hi Sebastiaan,
Is there a content switch in front? And are you testing direct to the virtual server? Or are there redirects configured?
Best regards, Jeroen.
Hi Jeroen,
There is a content switch virtual server in front. webmail.domain.com is redirected tot login.domain.com at LB level.
Thing is that I cannot bind rewrite policies to the Authentication Virtual Servers. Only to LB Virtual servers and CS Virtual Servers. I tried both but the result is the same. The website is graded with a D.
I did check the Goto expression value. Next, next, next, end.
-Sebastiaan
Hi Sebastiaan,
Default securityheaders.io will follow redirects (checkbox below the url box). So in your case the test will be performed against login.domain.com.
Jeroen.
Unchecking the follow redirects box leaves me with a grade R.
And all 5 header options are red. But it also shows a warning that says:
Warning: Grade capped at A, please see warnings below.
-Sebastiaan
In this blog post you find some more information. As you can’t bind the rewrite policies to an AAA vServer they will work if you bind them globally. Although they haven’t tested this on newer versions of the NetScaler. Now you have triggered me 😉 It’s gonna be a long night hahahaha. I will try to reproduce this myself.
https://discussions.citrix.com/topic/366082-netscaler-aaa-page-response-with-custom-header/
This aaa custom response link is broken. can we post the content here?
I also notice that the content security policy doesn’t work and when i use it as stated above, securityheaders.io shows it as not existing and gives me a B. any ideas?
This also could use an update in content to address similar reporting and header requirements in Bitsight since that’s what alot of companies are using now to track this kind of thing….
i did manage to get it up to an A by binding to the global default and not the global override so FYI for anyone if they run into same thing.
That being said. An A in Securityheaders.io doesn’t help me if the same config shows as “Fair” in bitsight
I’m going to check out the blog post and try to bind them globally. Thanks.
Hopefully you figure it out quickly 🙂 and you can enjoy your evening.
-Sebastiaan
Security Report Summary is showing “R” but all 6 headers are green. What might be the reason, its now showing A/A+?
Look at the whole report. There should be pointers in there.
“As long as Citrix implements “unsafe-inline” and “unsafe-eval” scripts in the Gateway we could not get it to work properly”
Does this mean you must have “unsafe-inline” and “unsafe-eval” in your CSP? My Security group keeps bouncing back because it’s failing scans. If I remove both values from my NetScaler CSP, the hosted site breaks. I run 11.0/71.22. Thanks.
Hi Jason, is you are happy with the A and not A+ then yes keep those in the CSP.
As long as Citrix implements “unsafe-inline” and “unsafe-eval” scripts in the Gateway we could not get it to work properly.
Does that mean the CSP MUST have both unsafe-inline and unsafe-eval due to NetScaler Gateway? It doesn’t work without it? I can’t see to get it to work if I remove those items.
Correct 😉
Apologies for the double comment. That’s too bad. We’re a payroll company and security is scrutinizing the unsafe-inline and unsafe-eval.
Thanks
Well tell your CSO that all fortune 500 companies are using the netscaler. If this was/is a security breach then it was already patch/known by Citrix. But what you can do is open a case by Citrix and let them come back with a decent answer 😉